VLAN Access Lists (VACLs)
VACLs can filter traffic within a VLAN and do not require a routed interface.
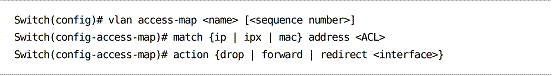
A VACL can match traffic from a MAC, IP, or IPX access list.
VACL configuration:
To apply a VACL to a VLAN:
Private VLANs
Private VLANs (PVLANs) can be implemented to prevent hosts within a VLAN from communicating directly.
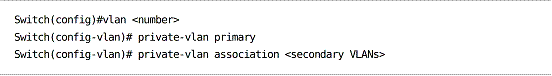
Primary (regular) VLANs are associated with secondary (private) VLANs.
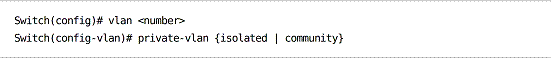
A secondary VLAN can be one of two types:
Isolated – Hosts associated with the VLAN can only reach the primary VLAN.
Community – Hosts can communicate with the primary VLAN and other hosts within the secondary VLAN, but not with other secondary VLANs.
PVLAN information is not communicated by VTP.
PVLAN ports are configured to operate in one of two modes:
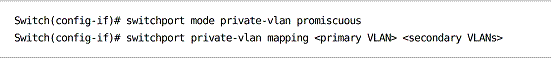
Promiscuous – Port attaches to a router, firewall, etc; can communicate with all hosts
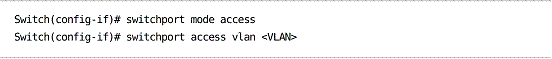
Host – Can only communicate with a promiscuous port, or ports within the same community PVLAN
Private VLAN Configuration
Defining a secondary PVLAN:
Defining a primary PVLAN:
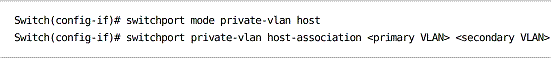
Designating a host port:
Designating a promiscuous port:
Host ports are associated with one primary and one secondary VLAN, whereas promiscuous ports are mapped to one primary and multiple secondary VLANs.
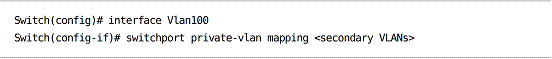
Secondary VLANs can be mapped to an SVI like a promiscuous port, but without the need to specify the primary VLAN:
Securing VLAN Trunks
Explicitly configure all access ports to protect against trunk spoofing:
VLAN hopping can be mitigated by ensuring an access VLAN is not used as the native VLAN of a trunk.