New Updated 400-251 Exam Questions from PassLeader 400-251 PDF dumps! Welcome to download the newest PassLeader 400-251 VCE dumps: http://www.passleader.com/400-251.html (366 Q&As)
Keywords: 400-251 exam dumps, 400-251 exam questions, 400-251 VCE dumps, 400-251 PDF dumps, 400-251 practice tests, 400-251 study guide, 400-251 braindumps, CCIE Security Exam
p.s. Free 400-251 dumps download from Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpd3JLalNVS0VWbms
QUESTION 61
Which command can you enter on the Cisco ASA to disable SSH?
A. Crypto key generate ecdsa label
B. Crypto key generate rsa usage-keys noconfirm
C. Crypto keys generate rsa general-keys modulus 768
D. Crypto keys generate ecdsa noconfirm
E. Crypto keys zeroize rsa noconfirm
Answer: E
QUESTION 62
Which one of the foiling Cisco ASA adapts security appliance rule samples will send HTTP data to the AIP-SSM module to evaluate and stop HTTP attacks?
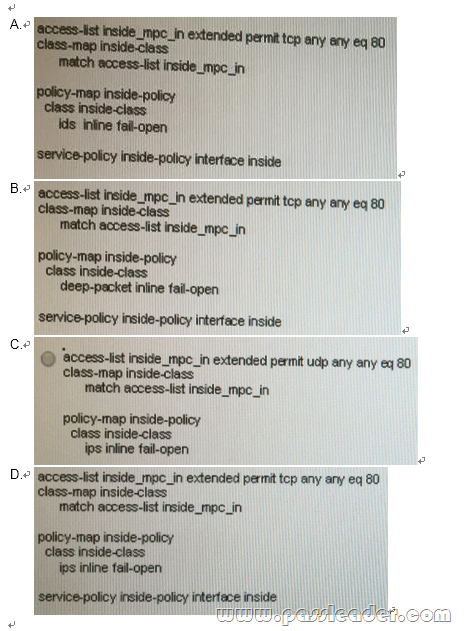
Answer: D
QUESTION 63
Why is the IPv6 type 0 routing header vulnerable to attack?
A. It allows the receiver of a packet to control its flow.
B. It allows the sender to generate multiple NDP requests for each packet.
C. It allows the sender of a packet to control its flow.
D. It allows the sender to generate multiple ARP requests for each packet.
E. It allows the receiver of a packet to modify the source IP address.
Answer: C
QUESTION 64
What context-based access control (CBAC. command sets the maximum time that a router running Cisco IOS Will wait for a new TCP session to reach the established state?
A. IP inspect max-incomplete
B. IP inspect tcp finwait-time
C. Ip inspect udp idle-time
D. Ip inspect tcpsynwait-time
E. Ip inspect tcp idle-time
Answer: D
QUESTION 65
Which three statements about Cisco Flexible NetFlow are true? (Choose three.)
A. The packet information used to create flows is not configurable by the user.
B. It supports IPv4 and IPv6 packet fields.
C. It tracks all fields of an IPv4 header as well as sections of the data payload.
D. It uses two types of flow cache, normal and permanent.
E. It can be a useful tool in monitoring the network for attacks.
Answer: BCE
QUESTION 66
What are the two most common methods that security auditors use to assess an organization’s security processes? (Choose two.)
A. social engineering attempts
B. interviews
C. policy assessment
D. penetration testing
E. document review
F. physical observations
Answer: AE
QUESTION 67
On Which encryption algorithm is CCMP based?
A. IDEA
B. BLOWFISH
C. RCS
D. 3DES
E. AES
Answer: E
QUESTION 68
By defaults which amount of time does the ASA add to the TTL value of a DNS entry to determine the amount of time a DNS entry is valid?
A. 60 seconds
B. 30 seconds
C. 0 second
D. 180 seconds
E. 120 seconds
F. 100 seconds
Answer: A
QUESTION 69
Drag and Drop Question
Drag and drop the desktop-security terms from the left onto their right definitions on the right. 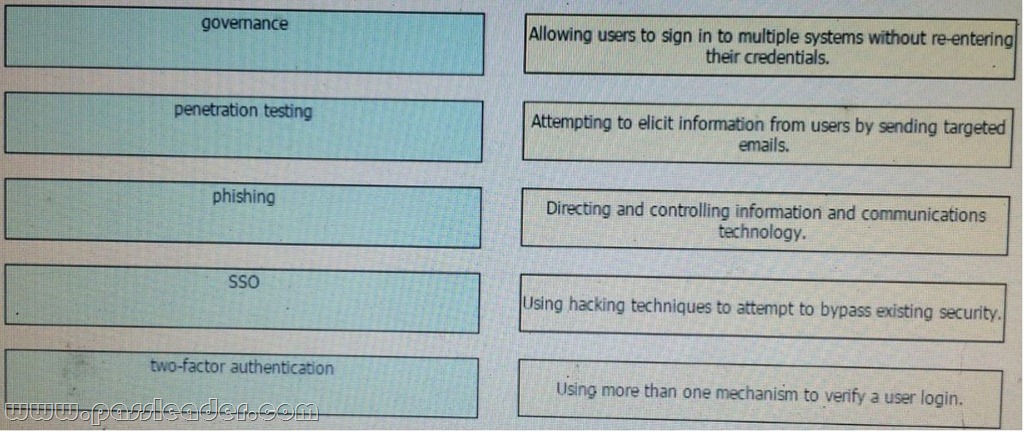
Answer: 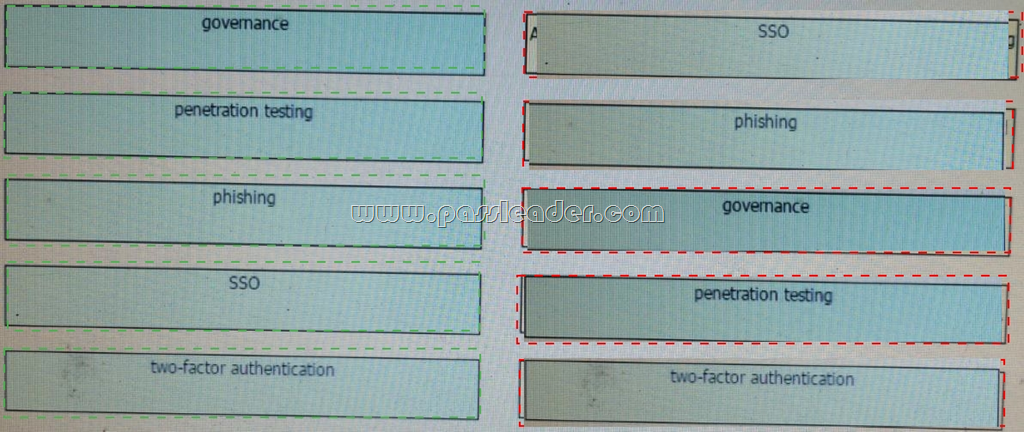
QUESTION 70
What is the name of the unique tool/feature in cisco security manager that is used to merge an access list based on the source/destination IP address service or combination of these to provide a manageable view of access policies?
A. merge rule tool
B. policy simplification tool
C. rule grouping tool
D. object group tool
E. combine rule tool
Answer: E
QUESTION 71
Refer to the exhibit. Which statement about the effect of this configuration is true? 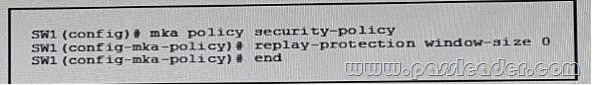
A. reply protection is disable
B. It prevent man-in-the-middle attacks
C. The replay window size is set to infinity
D. Out-of-order frames are dropped
Answer: D
QUESTION 72
when a host initiates a TCP session, what is the numerical range into which the initial sequence number must fail?
A. 0 to 65535
B. 1 to 1024
C. 0 to 4,294,967,295
D. 1 to 65535
E. 1 to 4,294,967,295
F. 0 to 1024
Answer: C
QUESTION 73
What port has IANA assigned to the GDOI protocol?
A. UDP 4500
B. UDP 500
C. UDP 1812
D. UDP 848
Answer: D
QUESTION 74
Drag and Drop Question
Drag each Cisco TrustSec feature on the left to its description on the right. 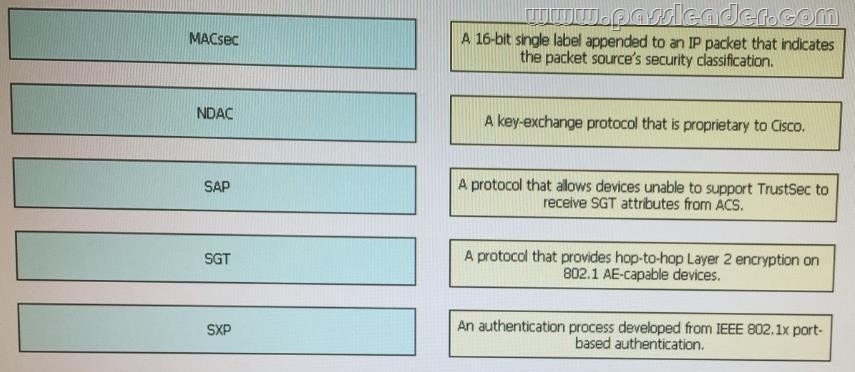
Answer: 
QUESTION 75
Which statement is true about SYN cookies?
A. The state is kept on the server machine TCP stack
B. A system has to check every incoming ACK against state tables
C. NO state is kept on the server machine state but is embedded in the initial sequence number
D. SYN cookies do not help to protect against SYN flood attacks
Answer: C
QUESTION 76
Refer to the exhibit. R1 and R2 are connected across and ASA with MD5 authentication. Which statement about eBGP peering between the routers could be true? 
A. eBGP peering will fail because ASA is transit lacks BGP support.
B. eBGP peering will be successful.
C. eBGP peering will fail because the two routers must be directly connected to allow peering.
D. eBGP peering will fail because of the TCP random sequence number feature.
Answer:
QUESTION 77
What is the maximum pattern length supported by FPM searches within a packet?
A. 256 bytes
B. 1500 bytes
C. 512 bytes
D. 128 bytes
Answer: A
QUESTION 78
Refer to the exhibit. What are three effect of the given firewall configuration? (Choose three.) 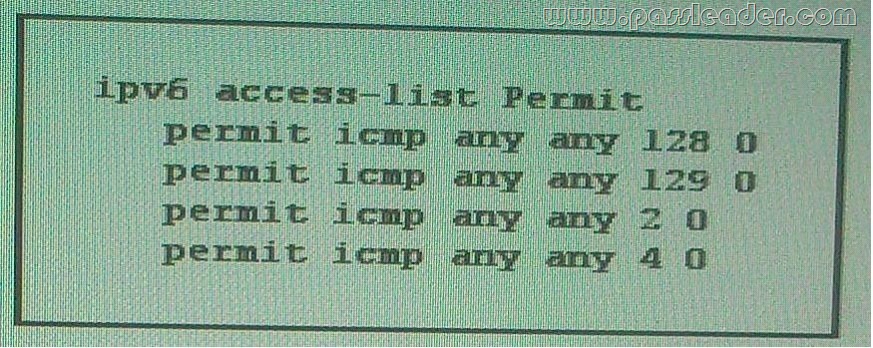
A. The firewall allows Echo Request packets from any source to pass server.
B. The firewall allows time Exceeded error messages from any source to pass to the server.
C. PCs outside the firewall are unable to communicate with the server over HTTP.
D. The firewall allows Echo Reply packets from any source to pass to the server.
E. The firewall allows Destination Unreachable error messages from any source to pass to the server.
F. The firewall allows Packet too big error messages from any source to pass to the server.
Answer: ADF
QUESTION 79
Refer to the exhibit Flexible NetFlow is failing to export flow records from RouterA to your flow collector. What action can you take to allow the IPv6 flow records to be sent to the collect? 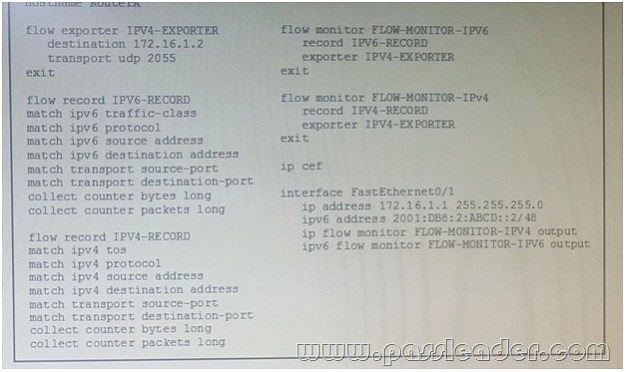
A. Set the NetFlow export protocol to v5
B. Configure the output-features command for the IPV4-EXPORTER
C. Add the ipv6 cef command to the configuration
D. Remove the ip cef command from the configuration
E. Create a new flow exporter with an IPv6 destination and apply it to the flow monitor
Answer: D
QUESTION 80
Drag and Drop Question
Drag each type of spoofing attack on the left to an action you can take to prevent it on the right. 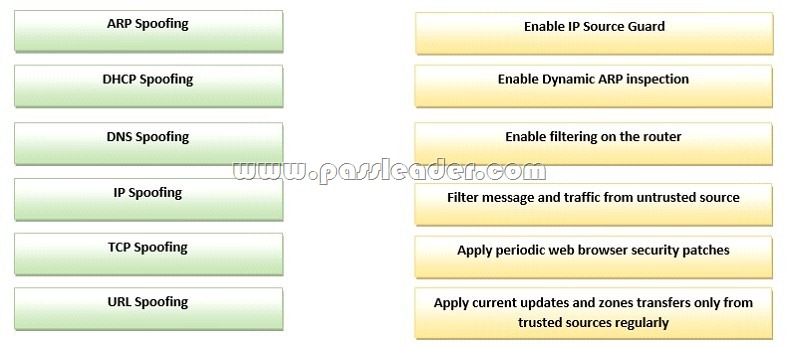
Answer: 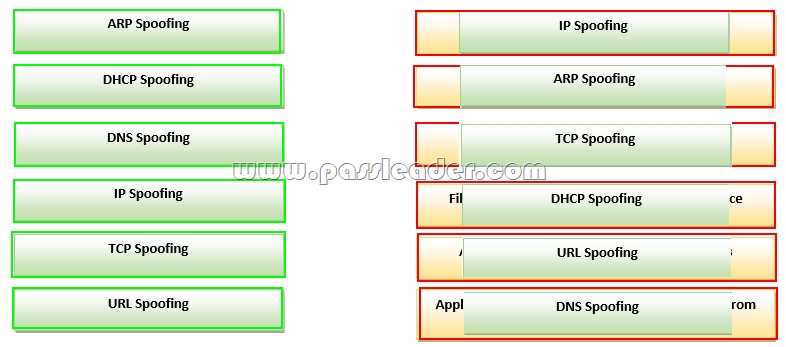
QUESTION 81
When you configure an ASA with RADIUS authentication and authorization, which attribute is used to differentiate user roles?
A. login-ip-host
B. cisco-priv-level
C. service-type
D. termination-action
E. tunnel-type
Answer: C
QUESTION 82
Which two statement about the IPv6 Hop-by-Hop option extension header (EH) are true? (Choose two.)
A. The Hop-by-Hop EH is processed in hardware at the source and the destination devices only.
B. If present, network devices must process the Hop-by-Hop EH first.
C. The Hop-by-Hop extension header is processed by the CPU by network devices.
D. The Hop-by-Hop EH is processed in hardware by all intermediate network devices.
E. The Hop-by-Hop EH is encrypted by the Encapsulating Security Header.
F. If present the Hop-by-Hop EH must follow the Mobility EH.
Answer: BC
QUESTION 83
Refer to the exhibit. Which configuration option will correctly process network authentication and authorization using both single port? 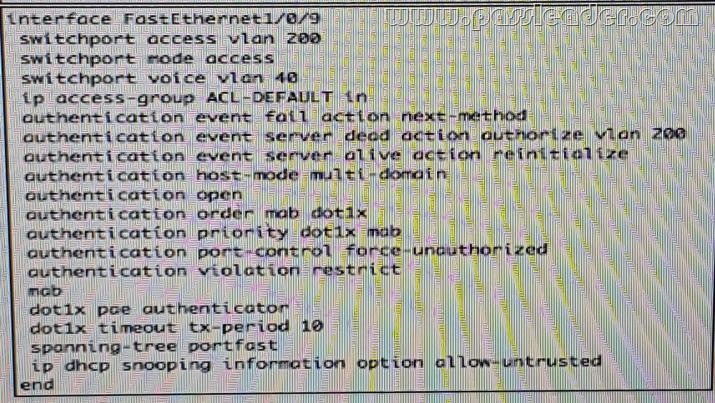
A.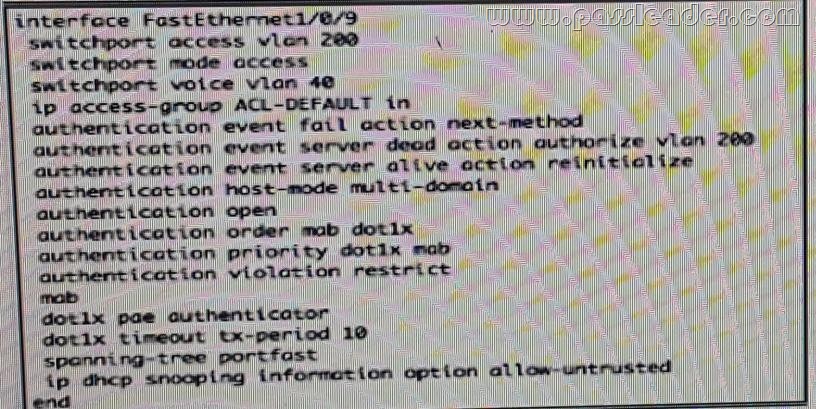
B.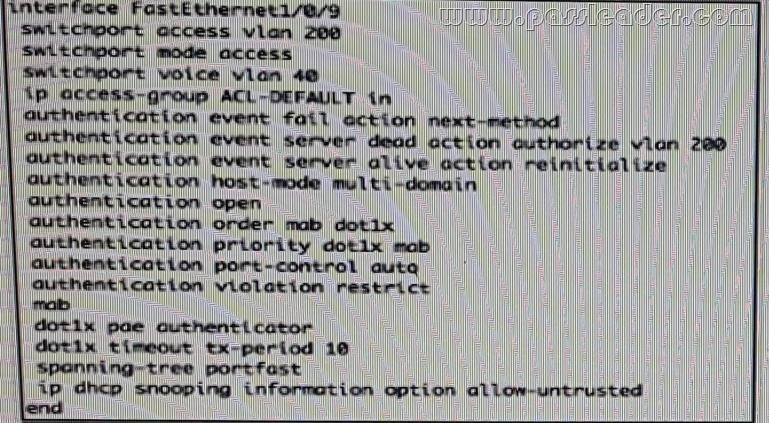
C.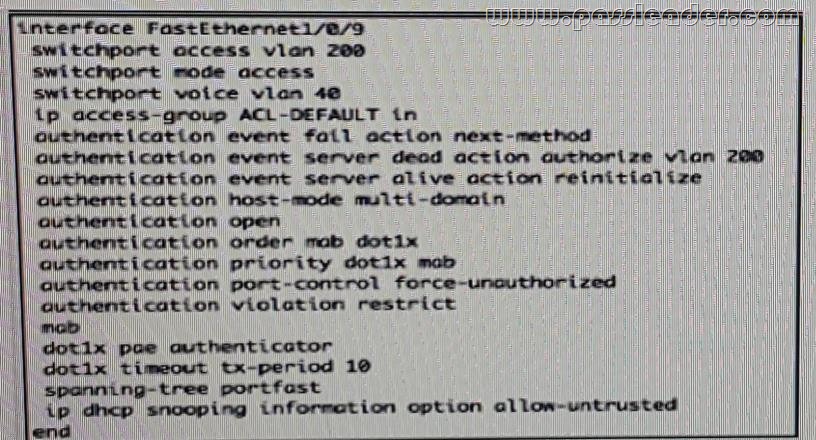
D.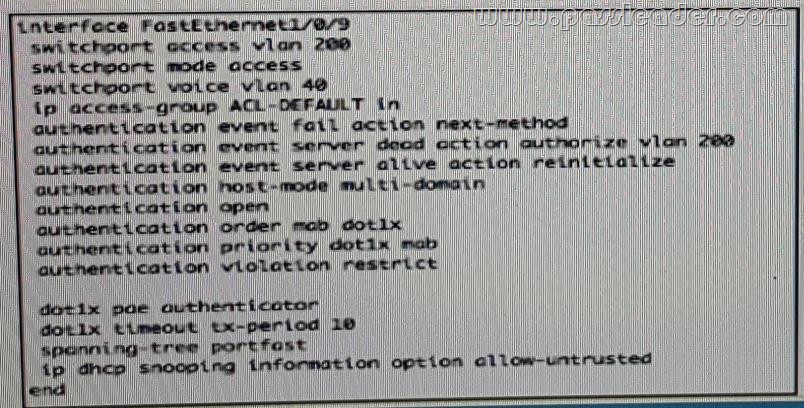
Answer: B
QUESTION 84
Which two current RFCs discuss special use IP addresses that may be used as a checklist of invalid routing prefixes for IPv4 and IPv6 addresses? (Choose two.)
A. RFC 5156
B. RFC 5735
C. RFC 3330
D. RFC 1918
E. RFC 2827
Answer: AB
QUESTION 85
What are two protocols that HTTP can use to secure sessions? (Choose two.)
A. HTTPS
B. AES
C. TLS
D. AH
E. SSL
Answer: AE
QUESTION 86
Which three statements about the IANA are true? (Choose three.)
A. IANA is a department that is operated by the IETF.
B. IANA oversees global IP address allocation.
C. IANA managed the root zone in the DNS.
D. IANA is administered by the ICANN.
E. IANA defines URI schemes for use on the Internet.
Answer: BCD
QUESTION 87
A cloud service provider is designing a large multilenant data center to support thousands of tenants. The provider is concerned about the scalability of the Layer 2 network and providing Layer 2 segmentation to potentially thousands of tenants. Which Layer 2 technology is best suited in this scenario?
A. LDP
B. VXLAN
C. VRF
D. Extended VLAN ranges
Answer: B
QUESTION 88
Refer to the exhibit. Which effect of this configuratioin is true? 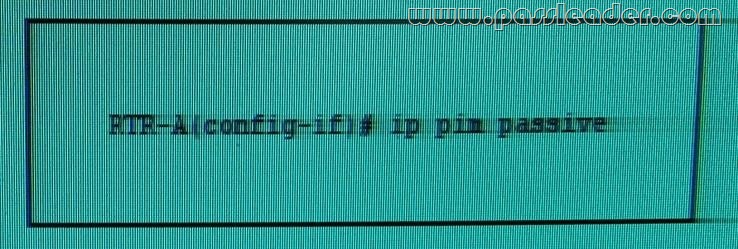
A. The router sends PIM messages only to other routers on the same LAN.
B. The router sends PIM messages, but it rejects any PIM message it receives.
C. The router acts as a stub multicast router for the EIGRP routing protocol.
D. The router accepts all PIM control messages.
E. The router acts as the DR and DF for all bidir-PIM group ranges.
Answer: E
QUESTION 89
What is the purpose of enabling the IP option selective Drop feature on your network routers?
A. To protect the internal network from IP spoofing attacks.
B. To drop IP fragmented packets.
C. To drop packet with a TTL value of Zero.
D. To protect the network from DoS attacks.
Answer: D
QUESTION 90
Which two answers describe provisions of the SOX Act and its international counterpart Acts? (Choose two.)
A. confidentiality and integrity of customer records and credit card information
B. accountability in the event of corporate fraud
C. financial information handled by entities such as banks, and mortgage and insurance brokers
D. assurance of the accuracy of financial records
E. US Federal government information
F. security standards that protect healthcare patient data
Answer: BD
Download the newest PassLeader 400-251 dumps from passleader.com now! 100% Pass Guarantee!
400-251 PDF dumps & 400-251 VCE dumps: http://www.passleader.com/400-251.html (366 Q&As) (New Questions Are 100% Available and Wrong Answers Have Been Corrected! Free VCE simulator!)
p.s. Free 400-251 dumps download from Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpd3JLalNVS0VWbms




