Port Security
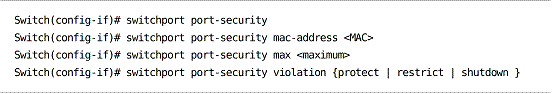
Port security can be used to restrict which or how many hosts connect to a switch port:
Violation actions:
protect – The port continues to function without logging a violation, but frames from violating MAC addresses are dropped.
restrict – As with protect mode, frames from violating MAC addresses are dropped, but the violation is logged.
shutdown – The port is transitioned to the error-disabled state, and no traffic is accepted.
IEEE 802.1x
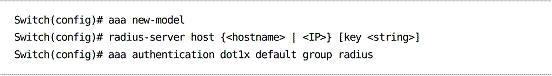
Extensible Authentication Protocol Over LANs (EAPOL) is used to authenticate a connecting host to a switch via layer 2.
Enable AAA and specify a RADIUS server to be referenced for authentication:
Enable 802.1x globally:
Configure authorization per interface:
Port control states:
Force – authorized (default) – Port is always authorized
Force – unauthorized – Port will never become authorized
Auto – Authorization depends on a successful 802.1x authentication
Multiple hosts can be allowed to share a single port with dot1x host-mode multi-host.
show dot1x all will verify 802.1x operation.
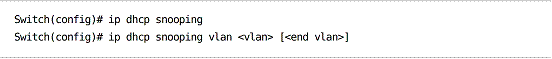
DHCP Snooping
DHCP Snooping prevents DHCP-influenced Man-in-the-Middle (MITM) attacks by blocking DHCP replies from untrusted ports.
To designate a port as trusted (DHCP replies are allowed inbound):
DHCP snooping can also rate-limit DHCP requests on untrusted ports:
A DHCP snooping switch can inject its own MAC and the port on which a request was received in option 82 of the request:
show ip dhcp snooping [binding] displays DHCP snooping status.
IP Source Guard
IP source guard is used to mitigate IP spoofing, and relies on DHCP snooping bindings to determine the legitimacy of a source address.
To enable IP source guard:
The addition of the port-security parameter also enables validation of source MAC addresses for ports configured with port security.
Static address mappings can be entered for hosts which do not use DHCP:
Verification:
show ip verify source – Displays the IP source guard status
show ip source binding – Displays the IP source guard database
Dynamic ARP Inspection (DAI)
DAI mitigates ARP spoofing attacks (ARP cache poisoning); static ARP entries or the DHCP snooping database must be used for reference.
To enable DAI per VLAN:
DAI is only performed on untrusted ports; all ports are untrusted by default.
To configure an interface as trusted:
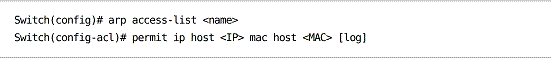
Static ARP entries can be defined in an ARP access list:
To apply the ARP ACL to one or more VLANs:
The static keyword disables checking against the DHCP snooping database (ARP replies will only be allowed from hosts listed in the ACL).
By default DAI only checks the ARP source MAC and IP. DAI can be configured to also inspect the Ethernet header source and destination MAC, and ARP source IP:
show ip arp inspection displays DAI status information.