New Updated 156-215.80 Exam Questions from PassLeader 156-215.80 PDF dumps! Welcome to download the newest PassLeader 156-215.80 VCE dumps: https://www.passleader.com/156-215-80.html (417 Q&As)
Keywords: 156-215.80 exam dumps, 156-215.80 exam questions, 156-215.80 VCE dumps, 156-215.80 PDF dumps, 156-215.80 practice tests, 156-215.80 study guide, 156-215.80 braindumps, Check Point Certified Security Administrator (CCSA) R80 Exam
P.S. New 156-215.80 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpdm81T0hOX1ZpWGs
NEW QUESTION 351
Customer’s R80 management server needs to be upgraded to R80.10. What is the best upgrade method when the management server is not connected to the Internet?
A. Export R80 configuration, clean install R80.10 and import the configuration.
B. CPUSE online upgrade.
C. CPUSE offline upgrade.
D. SmartUpdate upgrade.
Answer: C
NEW QUESTION 352
SmartEvent does NOT use which of the following procedures to identity events?
A. Matching a log against each event definition.
B. Create an event candidate.
C. Matching a log against local exclusions.
D. Matching a log against global exclusions.
Answer: C
NEW QUESTION 353
John is using Management HA. Which Smartcenter should be connected to for making changes?
A. secondary Smartcenter
B. active Smartcenter
C. connect virtual IP of Smartcenter HA
D. primary Smartcenter
Answer: B
NEW QUESTION 354
Which path below is available only when CoreXL is enabled?
A. Slow path
B. Firewall path
C. Medium path
D. Accelerated path
Answer: C
NEW QUESTION 355
Which of the following describes how Threat Extraction functions?
A. Detect threats and provides a detailed report of discovered threats.
B. Proactively detects threats.
C. Delivers file with original content.
D. Delivers PDF versions of original files with active content removed.
Answer: B
NEW QUESTION 356
The SmartEvent R80 Web application for real-time event monitoring is called what?
A. SmartView Monitor
B. SmartEventWeb
C. There is no Web application for SmartEvent
D. SmartView
Answer: B
NEW QUESTION 357
SandBlast offers flexibility in implementation based on their individual business needs. What is an option for deployment of Check Point SandBlast Zero-Day Protection?
A. Smart Cloud Services
B. Load Sharing Mode Services
C. Threat Agent Solution
D. Public Cloud Services
Answer: A
NEW QUESTION 358
What SmartEvent component creates events?
A. Consolidation Policy
B. Correlation Unit
C. SmartEvent Policy
D. SmartEvent GUI
Answer: B
NEW QUESTION 359
Which Threat Prevention Profile is not included by default in R80 Management?
A. Basic: Provides reliable protection on a range of non-HTTP protocols for servers, with minimal impact on network performance.
B. Optimized: Provides excellent protection for common network products and protocols against recent or popular attacks.
C. Strict: Provides a wide coverage for all products and protocols, with impact on network performance.
D. Recommended: Provides all protection for all common network products and servers, with impact on network performance.
Answer: D
NEW QUESTION 360
When using Monitored circuit VRRP, what is a priority delta?
A. When an interface fails the priority changes to the priority delta.
B. When an interface fails the delta claims the priority.
C. When an interface fails the priority delta is subtracted from the priority.
D. When an interface fails the priority delta decides if the other interfaces takes over.
Answer: C
NEW QUESTION 361
Which of the following is NOT an option to calculate the traffic direction?
A. Incoming
B. Internal
C. External
D. Outgoing
Answer: D
NEW QUESTION 362
When an encrypted packet is decrypted, where does this happen?
A. Security policy
B. Inbound chain
C. Outbound chain
D. Decryption is not supported
Answer: A
NEW QUESTION 363
Which of the following is NOT a component of Check Point Capsule?
A. Capsule Docs
B. Capsule Cloud
C. Capsule Enterprise
D. Capsule Workspace
Answer: C
NEW QUESTION 364
You have successfully backed up your Check Point configurations without the OS information. What command would you use to restore this backup?
A. restore_backup
B. import backup
C. cp_merge
D. migrate import
Answer: A
NEW QUESTION 365
What is the best sync method in the ClusterXL deployment?
A. Use 1 cluster + 1st sync
B. Use 1 dedicated sync interface
C. Use 3 clusters + 1st sync + 2nd sync + 3rd sync
D. Use 2 clusters + 1st sync + 2nd sync
Answer: B
NEW QUESTION 366
Can multiple administrators connect to a Security Management Server at the same time?
A. No, only one can be connected.
B. Yes, all administrators can modify a network object at the same time.
C. Yes, every administrator has their own username, and works in a session that is independent of other administrators.
D. Yes, but only one has the right to write.
Answer: C
NEW QUESTION 367
What Identity Agent allows packet tagging and computer authentication?
A. Endpoint Security Client
B. Full Agent
C. Light Agent
D. System Agent
Answer: B
NEW QUESTION 368
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
A. Accounting
B. Suppression
C. Accounting/Suppression
D. Accounting/Extended
Answer: C
NEW QUESTION 369
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don’t have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
A. fw ctl multik dynamic_dispatching on
B. fw ctl multik dynamic_dispatching set_mode 9
C. fw ctl multik set_mode 9
D. fw ctl miltik pq enable
Answer: C
NEW QUESTION 370
Which two of these Check Point Protocols are used by?
A. ELA and CPD
B. FWD and LEA
C. FWD and CPLOG
D. ELA and CPLOG
Answer: B
NEW QUESTION 371
To ensure that VMAC mode is enabled, which CLI command you should run on all cluster members?
A. fw ctl set int fwha vmac global param enabled
B. fw ctl get int fwha vmac global param enabled; result of command should return value 1
C. cphaprob -a if
D. fw ctl get int fwha_vmac_global_param_enabled; result of command should return value 1
Answer: B
NEW QUESTION 372
What is the SOLR database for?
A. Used for full text search and enables powerful matching capabilities.
B. Writes data to the database and full text search.
C. Serves GUI responsible to transfer request to the DLE server.
D. Enables powerful matching capabilities and writes data to the database.
Answer: A
NEW QUESTION 373
Which of the following commands is used to monitor cluster members?
A. cphaprob state
B. cphaprob status
C. cphaprob
D. cluster state
Answer: A
NEW QUESTION 374
Service blades must be attached to a ____.
A. Security Gateway
B. Management container
C. Management server
D. Security Gateway container
Answer: A
NEW QUESTION 375
An LDAP server holds one or more ____.
A. Server Units
B. Administrator Units
C. Account Units
D. Account Server
Answer: C
NEW QUESTION 376
In Security Gateways R75 and above, SIC uses ____ for encryption.
A. AES-128
B. AES-256
C. DES
D. 3DES
Answer: A
NEW QUESTION 377
What protocol is specifically used for clustered environments?
A. Clustered Protocol
B. Synchronized Cluster Protocol
C. Control Cluster Protocol
D. Cluster Control Protocol
Answer: D
NEW QUESTION 378
Which of the following is NOT a tracking option? (Select three.)
A. Partial log
B. Log
C. Network log
D. Full log
Answer: ACD
NEW QUESTION 379
Which command shows the installed licenses?
A. cplic print
B. print cplic
C. fwlic print
D. show licenses
Answer: A
NEW QUESTION 380
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
A. SmartManager
B. SmartConsole
C. Security Gateway
D. Security Management Server
Answer: C
NEW QUESTION 381
Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
A. all options stop Check Point processes
B. backup
C. migrate export
D. snapshot
Answer: D
NEW QUESTION 382
What is the Transport layer of the TCP/IP model responsible for?
A. It transports packets as datagrams along different routes to reach their destination.
B. It manages the flow of data between two hosts to ensure that the packets are correctly assembled and delivered to the target application.
C. It defines the protocols that are used to exchange data between networks and how host programs interact with the Application layer.
D. It deals with all aspects of the physical components of network connectivity and connects with different network types.
Answer: B
NEW QUESTION 383
What needs to be configured if the NAT property `Translate destination on client side’ is not enabled in Global properties?
A. A host route to route to the destination IP.
B. Use the file local.arp to add the ARP entries for NAT to work.
C. Nothing, the Gateway takes care of all details necessary.
D. Enabling `Allow bi-directional NAT’ for NAT to work correctly.
Answer: C
NEW QUESTION 384
In the Check Point Security Management Architecture, which component(s) can store logs?
A. SmartConsole
B. Security Management Server and Security Gateway
C. Security Management Server
D. SmartConsole and Security Management Server
Answer: B
NEW QUESTION 385
In order to install a license, it must first be added to the ____.
A. User Center
B. Package repository
C. Download Center Web site
D. License and Contract repository
Answer: B
NEW QUESTION 386
When logging in for the first time to a Security management Server through SmartConsole, a fingerprint is saved to the …?
A. Security Management Server’s /home/.fgpt file and is available for future SmartConsole authentications.
B. Windows registry is available for future Security Management Server authentications.
C. There is no memory used for saving a fingerprint anyway.
D. SmartConsole cache is available for future Security Management Server authentications.
Answer: D
NEW QUESTION 387
By default, the SIC certificates issued by R80 Management Server are based on the ____ algorithm.
A. SHA-256
B. SHA-200
C. MD5
D. SHA-128
Answer: A
NEW QUESTION 388
Which message indicates IKE Phase 2 has completed successfully?
A. Quick Mode Complete
B. Aggressive Mode Complete
C. Main Mode Complete
D. IKE Mode Complete
Answer: A
NEW QUESTION 389
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base: 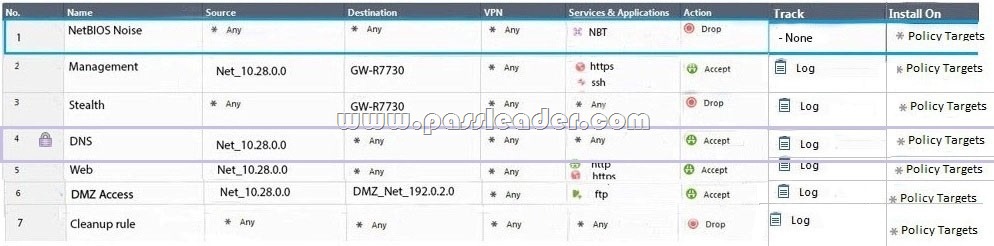
What is the possible explanation for this?
A. DNS Rule is using one of the new feature of R80 where an administrator can mark a rule with the padlock icon to let other administrators know it is important.
B. Another administrator is logged into the Management and currently editing the DNS Rule.
C. DNS Rule is a placeholder rule for a rule that existed in the past but was deleted.
D. This is normal behavior in R80 when there are duplicate rules in the Rule Base.
Answer: B
NEW QUESTION 390
When tunnel test packets no longer invoke a response, SmartView Monitor displays ____ for the given VPN tunnel.
A. Down
B. No Response
C. Inactive
D. Failed
Answer: A
NEW QUESTION 391
Which of the following is the most secure means of authentication?
A. Password
B. Certificate
C. Token
D. Pre-shared secret
Answer: B
NEW QUESTION 392
What is the BEST command to view configuration details of all interfaces in Gaia CLISH?
A. ifconfig -a
B. show interfaces
C. show interfaces detail
D. show configuration interface
Answer: D
NEW QUESTION 393
Authentication rules are defined for ____.
A. user groups
B. users using UserCheck
C. individual users
D. all users in the database
Answer: A
NEW QUESTION 394
Which tool provides a list of trusted files to the administrator so they can specify to the Threat Prevention blade that these files do not need to be scanned or analyzed?
A. ThreatWiki
B. Whitelist Files
C. AppWiki
D. IPS Protections
Answer: A
NEW QUESTION 395
Which of the following is an authentication method used for Identity Awareness?
A. SSL
B. Captive Portal
C. PKI
D. RSA
Answer: B
NEW QUESTION 396
The SIC Status "Unknown" means what?
A. There is connection between the gateway and Security Management Server but it is not trusted.
B. The secure communication is established.
C. There is no connection between the gateway and Security Management Server.
D. The Security Management Server can contact the gateway, but cannot establish SIC.
Answer: C
NEW QUESTION 397
What is a reason for manual creation of a NAT rule?
A. In R80 all Network Address Translation is done automatically and there is no need for manually defined NAT-rules.
B. Network Address Translation of RFC1918-compliant networks is needed to access the Internet.
C. Network Address Translation is desired for some services, but not for others.
D. The public IP-address is different from the gateway’s external IP.
Answer: D
NEW QUESTION 398
Which of the following commands is used to verify license installation?
A. Cplic verify license
B. Cplic print
C. Cplic show
D. Cplic license
Answer: B
NEW QUESTION 399
To enforce the Security Policy correctly, a Security Gateway requires ____.
A. a routing table
B. awareness of the network topology
C. a Demilitarized Zone
D. a Security Policy install
Answer: B
NEW QUESTION 400
Which configuration element determines which traffic should be encrypted into a VPN tunnel vs. sent in the clear?
A. The firewall topologies
B. NAT Rules
C. The Rule Base
D. The VPN Domains
Answer: C
NEW QUESTION 401
……
Download the newest PassLeader 156-215.80 dumps from passleader.com now! 100% Pass Guarantee!
156-215.80 PDF dumps & 156-215.80 VCE dumps: https://www.passleader.com/156-215-80.html (417 Q&As) (New Questions Are 100% Available and Wrong Answers Have Been Corrected! Free VCE simulator!)
P.S. New 156-215.80 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpdm81T0hOX1ZpWGs




