New Updated 400-251 Exam Questions from PassLeader 400-251 PDF dumps! Welcome to download the newest PassLeader 400-251 VCE dumps: http://www.passleader.com/400-251.html (366 Q&As)
Keywords: 400-251 exam dumps, 400-251 exam questions, 400-251 VCE dumps, 400-251 PDF dumps, 400-251 practice tests, 400-251 study guide, 400-251 braindumps, CCIE Security Exam
p.s. Free 400-251 dumps download from Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpd3JLalNVS0VWbms
QUESTION 211
Refer to the exhibit. Which statement about the router R1 is true? 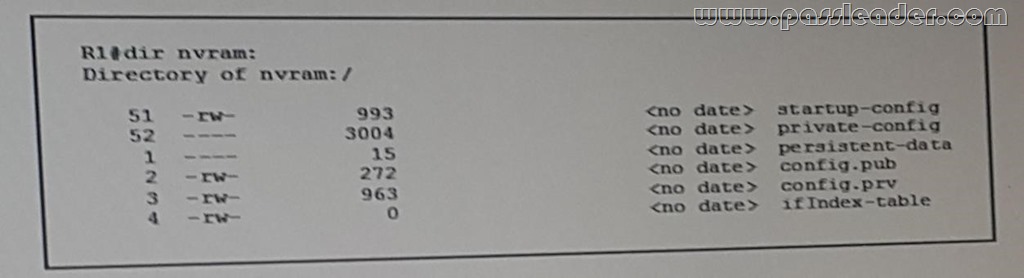
A. Its private-config is corrupt.
B. Its NVRAM contains public and private crypto keys.
C. Its running configuration is missing.
D. RMON is configured.
Answer: B
QUESTION 212
Refer to the Exhibit. What is the effect of the given ACL policy? 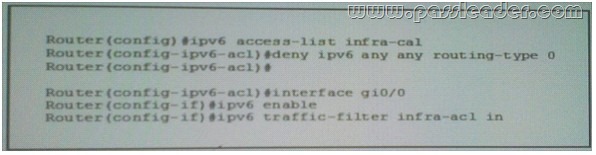
A. The policy will deny all IPv6 eBGP session.
B. The policy will disable IPv6 source routing.
C. The policy will deny all IPv6 routing packet.
D. The policy will deny all IPv6 routed packet.
Answer: B
QUESTION 213
Which three statements about the RSA algorithm are true? (Choose three.)
A. The RSA algorithm provides encryption but not authentication.
B. The RSA algorithm provides authentication but not encryption.
C. The RSA algorithm creates a pair of public-private keys that are shared by entities that perform encryption.
D. The private key is never sent across after it is generated.
E. The public key is used to decrypt the message that was encrypted by the private key.
F. The private key is used to decrypt the message that was encrypted by the public key.
Answer: CDF
QUESTION 214
Which of these is a core function of the risk assessment process? (Choose one.)
A. performing regular network upgrades
B. performing network optimization
C. performing network posture validation
D. establishing network baselines
E. prioritizing network roll-outs
Answer: C
QUESTION 215
Which two router configurations block packets with the Type 0 Routing header on the interface? (Choose two.)
A. Ipv6 access-list Deny_Loose_Routing
permit ipv6 any any routing-type 0
deny ipv6 any any
interface FastEthernet0/0
ipv6 traffic-filter Deny_Loose_Source_Routing in
B. Ipv6 access-list-Deny_Loose_Source_Routing
Deny ipv6 FE80::/10 any mobility -type bind-refresh
Interface FastEthernet/0
Ipv6 tr
Affic-filter Deny_Loose_Source_Routing in
C. Ipv6 access-list Deny_Loose_Source_Routing
Deny ipv6 any any routing-type 0
Permit ipv6 any any
Interface FastEthernet0/0
Ipv6 traffic -filter Deny_Loose_Routing in
D. Ipv6 access -list Deny_Loose_Source_Routing
Deny ipv6 any FE80: :/10 routing -type 0
Deny ipv6 any any routing -type 0
Permit ipv6 any any
Interface FastEthernet t0/0
Ipv6 traffic -filter Deny_Loose_Source_Routing in
E. Ipv6 access -list Deny_Loose_Source_Routing
Sequence 1 deny ipv6 any any routing -type 0 log-input
Sequence 2 permit ipv6 any any flow -label 0 routing interface Fastethernet0/0
Ipv6 traffic-filter Deny_Loose_Source_Routing in
Answer: CD
QUESTION 216
What protocol provides security for datagram protocols?
A. MAB
B. DTLS
C. SCEP
D. GET
E. LDP
Answer: B
QUESTION 217
Which two options are open-source SDN controllers? (Choose two.)
A. OpenContrail
B. OpenDaylight
C. Big Cloud Fabric
D. Virtual Application Networks SDN Controller
E. Application Policy Infrastructure Controller
Answer: AB
QUESTION 218
Which current RFC made RFCs 2409, 2407, and 2408 obsolete?
A. RFC 4306
B. RFC 2401
C. RFC 5996
D. RFC 4301
E. RFC 1825
Answer: A
QUESTION 219
Refer to the exhibit. Which effect of this configuration is true? 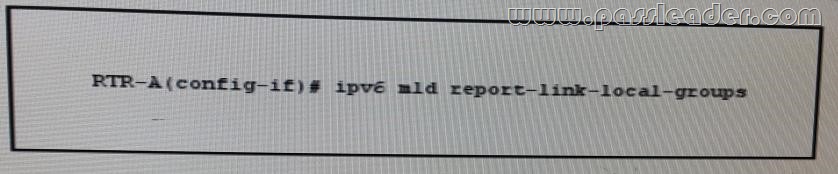
A. It enables MLD query messages for all link-local groups.
B. It configures the node to generate a link-local group report when it joins the solicited- node multicast group.
C. It enables hosts to send MLD report messages for groups 224.0.0.0/24.
D. it enables local group membership for MLDv1 and MLDv2.
E. It enables the host to send MLD report messages for nonlink local groups.
Answer: C
QUESTION 220
Which technology builds on the vPathconcept and can be used in virtual and physical environments?
A. VXLAN
B. ACI
C. NSH
D. SDN
Answer: C
QUESTION 221
Which two statements about header attacks are true? (Choose two.)
A. An attacker can use IPv6 Next Header attacks to steal user data and launch phishing attacks.
B. An attacker can use HTTP Header attacks to launch a DoS attack.
C. An attacker can execute a spoofing attack by populating the RH0 routing header subtype with multiple destination addresses.
D. An attacker can leverage an HTTP response header to write malicious cookies.
E. An attacker can leverage an HTTP response header to inject malicious code into an application layer.
F. An attacker can use vulnerabilities in the IPv6 routing header to launch attacks at the application layer.
Answer: BC
QUESTION 222
Refer to the exhibit. Routers R1, R2, and R3 have IPv6 reachability, and R1 and R3 are able to ping each other with the IPv6 global unicast address. However, R1 and R3 are unable to ping each other with their link-local addresses. What is a possible reason for the problem? 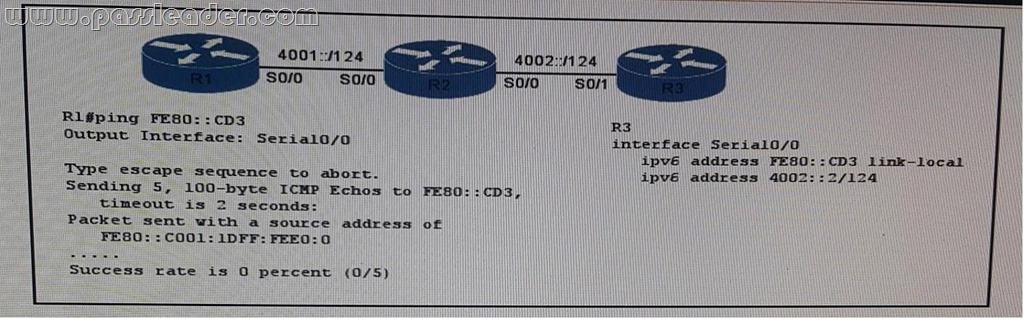
A. Link-local addresses can communicate with neighboring interfaces.
B. Link-local addresses are forwarded by IPv6 routers using loopback interfaces.
C. Link-local addresses can be used only with a physical interface’s local network.
D. Multicast must be enabled to allow link-local addresses to traverse multiple hops.
Answer: C
QUESTION 223
What is the effect of the Cisco Application Control Engine (ACE. command ipv6 fragment min-mtu 1024?
A. It configures the interface to fragment packets on connections with MTUs of 1024 or greater
B. It sets the MTU to 1024 bytes for an IPv6 VLAN interface that accepts fragmented packets
C. It configures the interface to attempt to reassemble only IPv6 fragments that are less than 1024 bytes
D. It configures the interface to fragment packets on connections with MTUs of 1024 or less
E. It configures the interface to attempt to reassemble only IPv6 fragments that are at least 1024 bytes
Answer: E
QUESTION 224
Which Two statement about the PCoIP protocol are true? (Choose two.)
A. It support both loss and lossless compression.
B. It is a client-rendered, multicast-codec protocol.
C. It is available in both software and hardware.
D. It is a TCP-based protocol.
E. It uses a variety of codec to support different operating system.
Answer: AC
QUESTION 225
Drag and Drop Question
Drag the step in the SCEP workflow on the left into the correct order of operation on the right. 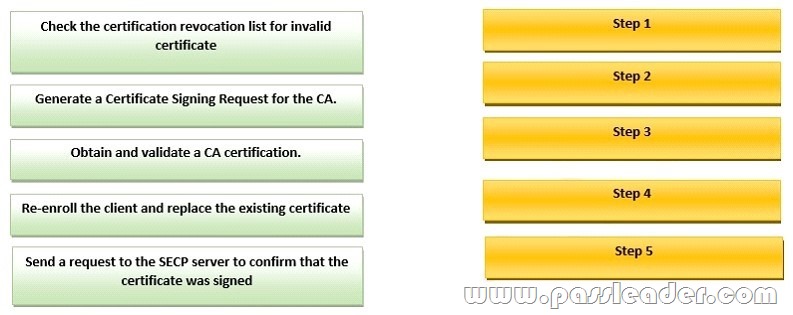
Answer: 
QUESTION 226
What are the two technologies that support AFT? (Choose two.)
A. NAT-PT
B. SNAT
C. NAT64
D. DNAT
E. NAT-PMP
F. NAT-6to4
Answer: AC
QUESTION 227
According to RFC 2577, Which two options describe drawbacks of the FTP protocol? (Choose two.)
A. If access to the FTP server is restricted by network address, the server still is susceptible to spoofing attacks.
B. Servers that apply connection limits to protect against brute force attacks are vulnerable to DoS attacks.
C. It is susceptible to man-m-the-middle attacks.
D. An attacker can validate user names if the 331 response is in use.
E. It is susceptible to bounce attacks on port 1024.
Answer: DE
QUESTION 228
Refer to the exhibit. Which two effects of this configuration are true? (Choose two.) 
A. The BGP neighbor session tears down after R1 receives 100 prefixes from the neighbor 1.1.1.1
B. The BGP neighbor session between R1 and R2 re-establishes after 50 minutes
C. A warning message is displayed on R2 after it receives 50 prefixes
D. A warning message is displayed on R2 after it receives 100 prefixes from neighbor 1.1.1.1
E. The BGP neighbor session tears down after R1 receives 200 prefixes from neighbor 2.2.2.2
F. The BGP neighbor session between R1 and R2 re-establishes after 100 minutes
Answer: DE
QUESTION 229
Drag and Drop Question
Drag and drop the DNS record types from the left to the matching descriptions to the right. 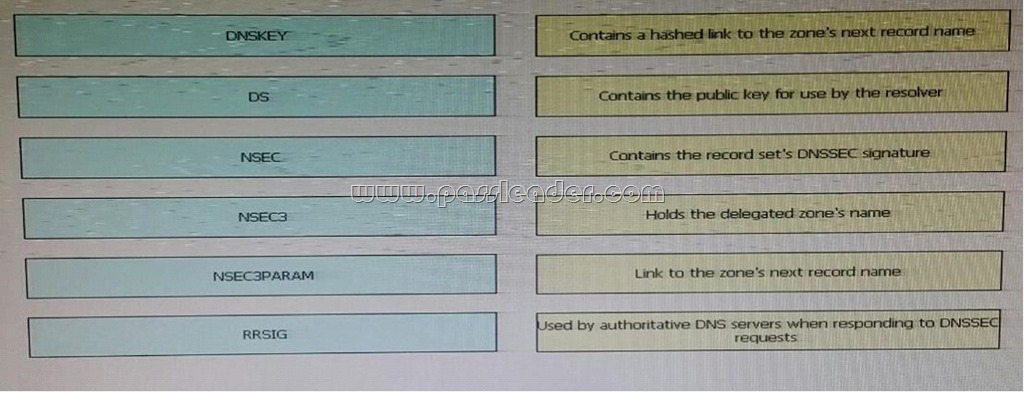
Answer: 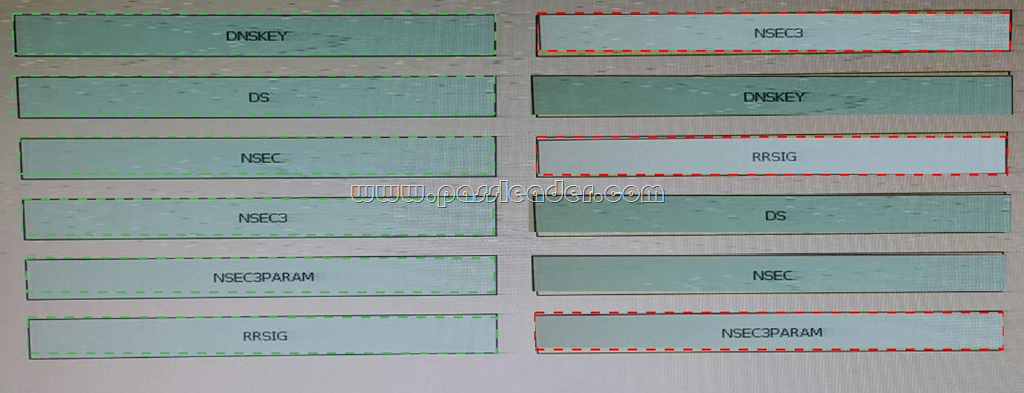
QUESTION 230
Which two statements describe the Cisco TrustSec system correctly? (Choose two.)
A. The Cisco TrustSec system is a partner program, where Cisco certifies third-party security products as extensions to the secure infrastructure.
B. The Cisco TrustSec system is an approach to certifying multimedia and collaboration applications as secure.
C. The Cisco TrustSec system is an Advanced Network Access Control System that leverages enforcement intelligence in the network infrastructure.
D. The Cisco TrustSec system tests and certifies all products and product versions that make up the system as working together in a validated manner.
Answer: CD
QUESTION 231
Which two statement about DTLS are true ? (Choose two.)
A. Unlike TLS,DTLS support VPN connection with ASA.
B. It is more secure that TLS.
C. When DPD is enabled DTLS connection can automatically fall back to TLS.
D. It overcomes the latency and bandwidth problem that can with SSL.
E. IT come reduce packet delays and improve application performance.
F. It support SSL VPNs without requiring an SSL tunnel.
Answer: CD
QUESTION 232
NWhich two statements about the ISO are true? (Choose two.)
A. The ISO is a government-based organization.
B. The ISO has three membership categories: Member, Correspondent, and Subscribers.
C. Subscriber members are individual organizations.
D. Only member bodies have voting rights.
E. Correspondent bodies are small countries with their own standards organization.
Answer: BD
Explanation:
Member bodies are national bodies considered the most representative standards body in each country. These are the only members of ISO that have voting rights.
QUESTION 233
Drag and Drop Question
Drag each SSI encryption algorithm on the left to the encryption and hashing values it uses on the right. 
Answer: 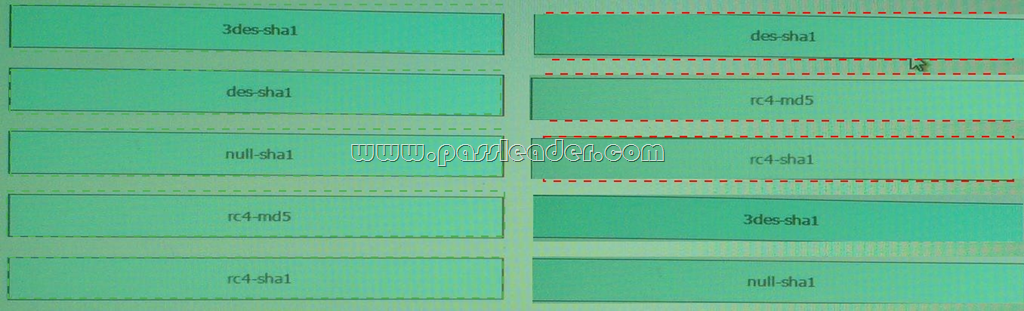
QUESTION 234
Drag and Drop Question
Drag and drop the role on the left onto their responsibility in the change-management process on the right. 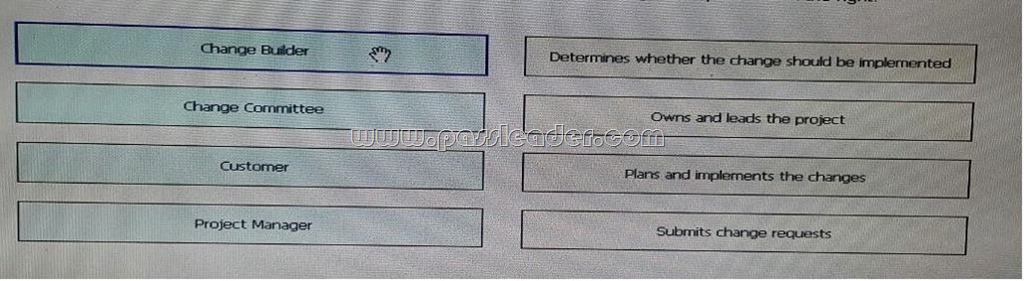
Answer: 
QUESTION 235
Refer to the exhibit, which as-path access-list regular expression should be applied on R2 as a neighbor filter list to only allow update with and origin of AS 65503? 
A. _65509.?$
B. _65503$
C. ^65503.*
D. ^65503$
E. _65503_
F. 65503
Answer: C
QUESTION 236
Which two commands would enable secure logging on Cisco ASA to a syslog server at 10.0.0.1? (Choose two.)
A. logging host inside 10.0.0.1 TCP/1500 secure
B. logging host inside 10.0.0.1 UDP/514 secure
C. logging host inside 10.0.0.1 TCP/1470 secure
D. logging host inside 10.0.0.1 UDP/500 secure
E. logging host inside 10.0.0.1 UDP/447 secure
Answer: AC
QUESTION 237
What feature enables extended secure access from non-secure physical location?
A. Port security
B. Strom control
C. NEAT
D. CBAC
E. 802 1x pot-based authentication
Answer: C
QUESTION 238
Which of the following best describes Chain of Evidence in the context of security forensics?
A. Evidence is locked down, but not necessarily authenticated.
B. Evidence is controlled and accounted for to maintain its authenticity and integrity.
C. The general whereabouts of evidence is known.
D. Someone knows where the evidence is and can say who had it if it is not logged.
Answer: B
QUESTION 239
What are three ways you can enforce a BCP38 policy on an internet edge policy? (Choose three.)
A. Avoid RFC1918 internet addressing.
B. Implement Cisco Express Forwarding.
C. Implement Unicast RPF.
D. Apply ingress filters for RFC1918 addresses.
E. Apply ingress ACL filters for BOGON routes.
F. Implement source NAT.
Answer: BCE
QUESTION 240
Which three addresses are special uses as defined in RFC 5735? (Choose three.)
A. 171.10.0.0/24
B. 0.0.0.0/8
C. 203.0.113.0/24
D. 192.80.90.0/24
E. 172.16.0.0/12
F. 198.50.100.0/24
Answer: BCE
Download the newest PassLeader 400-251 dumps from passleader.com now! 100% Pass Guarantee!
400-251 PDF dumps & 400-251 VCE dumps: http://www.passleader.com/400-251.html (366 Q&As) (New Questions Are 100% Available and Wrong Answers Have Been Corrected! Free VCE simulator!)
p.s. Free 400-251 dumps download from Google Drive: https://drive.google.com/open?id=0B-ob6L_QjGLpd3JLalNVS0VWbms




